Author: Joseph Moran
Review Date: 6/21/2006
Prior to the existence of the Internet as we know it today, if you needed a secure connection between two systems on remote networks, your choices were essentially to use a dedicated high-speed circuit like a T1 line or to rely on a slow modem, with both options often getting quite expensive.
These connection methods were largely supplanted by the advent of virtual private networks (VPNs), which have made connecting remote computers significantly cheaper by setting up an encrypted and “tunneled” connection across the Internet, allowing multiple computers or networks to communicate securely across an inherently insecure medium.
The catch with VPNs, however, is that they can be hard to set up. By contrast, Applied Networking Inc., rather confidently calls its Hamachi software a zero-config VPN application. We found that Hamachi does, in fact, make setting up a secure connection between systems a relatively simple affair that could easily be performed even by someone without significant networking expertise.
How Hamachi Works
There are several reasons that conventional VPN configuration can be so difficult. For starters, differences in implementation between manufacturers of routers, firewalls and client software can and often do cause interoperability problems. And even if you’re using the same equipment or software on both ends, a VPN can be a pain in the neck when you’re trying to connect two networks using network address translation (NAT).
NAT is used on countless networks these days and lets multiple systems on a private LAN communicate with the Internet using a single public IP address. The problem is that in order to translate the addresses between the private and public networks, NAT must modify the address information within network packets. This usually prevents VPNs from working because the modified packets are interpreted as having been compromised.
To get around the various obstacles to a successful VPN connection, Hamachi borrows a technique used by peer-to-peer applications such as instant messaging (IM) software. It employs an external server it calls a mediation server that acts as a sort of directory and matchmaker for Hamachi clients. The mediation server authenticates clients through the exchange of encryption keys, tracks clients so they can locate each other behind routers and firewalls and helps facilitate the setting up of secure connection between systems.
Applied Networking claims that once the mediation server has successfully established a connection between Hamachi clients, the secure connection is solely between the peers and no encrypted traffic passes through Hamachi servers. (The server does send regular keep-alive signals to clients, however, in order to keep idle connections up and running.)
Installation and Setup
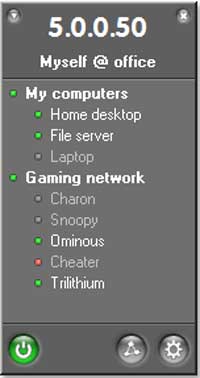
Hamachi uses a very minimalist interface that’s simple and easy to use. The first time you run the software a brief tutorial takes you through a tour of the interface, but it’s almost unnecessary since there are just three buttons on the client — the power button activates the Hamachi interface, the network button lets you create or join an existing network, and the gear button is for configuring application settings — of which there are only a handful.
When you install Hamachi, it creates its own virtual network interface on your system that has configuration parameters separate from those of your regular wired or wireless adapters. This Hamachi interface can be found alongside the others when you view your network connections in Windows, but it remains disabled until you turn on Hamachi using the aforementioned power button.
To create or join a Hamachi network, you click the network button and are prompted to supply a network name and password. As the connection is established, the Hamachi network interface is assigned its own IP address in a range separate from the one you’re already using. For example, our test system’s physical network adapter was configured with an address in the 192.168.1.x range, but our Hamachi adapter’s IP address was assigned 5.40.88.144. (Although this address is technically a public IP address, in this case it’s accessible only through the Hamachi network.)
Making Connections with Hamachi
Other systems can join a Hamachi network provided they know the network’s name and have the password. If our experience is any indication, users ought to have little if any difficulty connecting to each other via Hamachi. In fact, we were easily able to connect to a colleague’s Hamachi network across the Internet even though both networks were using different routers and NAT address ranges.
Connecting via Hamachi worked equally well no matter which end initiated the connection, and even more impressive was the fact that it established the link without the need to open ports or perform any kind of router/firewall configuration on either end. Since most software firewalls will recognize the Hamachi adapter as a separate network connection and block traffic on it, you may need to configure that firewall to allow the kinds of traffic you want over the Hamachi interface.
We were able to use Hamachi for a variety of tasks, including running Windows File and Printer sharing, an FTP server and for gaming. You can have multiple Hamachi networks active at one time, and all the clients that are members of a given network are listed in the interface (they’re grayed out if not currently connected). When you right-click on a network member you can ping the user’s system or send a text message, and if you’re the owner of the network, disconnect a system and prevent it from reconnecting in the future.
As mentioned earlier, Hamachi offers very little in the way of configuration options. That’s probably a good thing because the software unfortunately lacks documentation, a built-in help system or even a readme file (though there is evidently a support forum available at the company’s Web site). Most of the configuration options that exist are self-explanatory and concern how the software displays information or behaves during startup or shutdown.
The Bottom Line
Hamachi is currently available for Windows (XP and 2000 only) and Linux, with a MacOS version also under development according to the company. Hamachi is currently available free of charge for unlimited use but, given that it’s a pre-1.0 copy, it wouldn’t be surprising if the next version had some restrictions and/or a registration fee.
So exactly how secure is Hamachi? That’s hard to say definitively, since we’re neither cryptographers nor experts in network security. One thing to be aware of is that unlike most commercial VPN products, Hamachi authenticates only systems and not individual users (since all users connect using the same network name and password). Therefore, anyone that knows this information could potentially become a member of your secure network.
Given that the trust most people put in a product ultimately depends on the trustworthiness of the company that made it, the fact that Applied Networking is for the most part an unknown quantity may be enough to give some people cause for concern. And although the company’s .cc domain denotes a Cocos (Keeling) Islands registration, it’s actually located in Vancouver, BC, Canada — the .cc domain is commonly used by large companies worldwide.
For its part, Applied Networking states that it secures Hamachi communications using 256-bit AES encryption; it also publishes a detailed description of its security architecture on its Web site. For what it’s worth, the company also pledges that Hamachi doesn’t include any kind of spyware, and we didn’t detect any after installing the software.
We probably wouldn’t be quite comfortable transmitting truly sensitive information over a Hamachi connection right now, and we would only use it with someone we trusted to keep the network name and password private. Nevertheless, it’s hard to argue with Hamachi’s impressive ease of connection, so if you’re looking for a simple VPN that won’t make you pull your hair out, Hamachi is definitely worth a look.
Pros: Extremely easy to set up and use; works through NAT without any router adjustments; attractive (if rather Spartan) interface
Cons: No documentation; authenticates systems rather than specific users; relatively unknown company, making it hard to gage how secure the software ultimately is
Courtesy of Winplanet.com.




