If you’re experiencing problems with your network, the first step is to identify the issue. This can be done through a network stability test.
Whether they’re major or minor, network connection outages can occur on a regular basis, and even the best of us are not immune to them.
In this blog post, we will discuss what a network stability test is, show you how to use Ping and other professional tools to perform a network stability test, and how to use it to resolve any issues you may be having.
A network stability test is a check for the overall health of a network and the identification of problems or weak spots before they cause a crash. As a result, the definition of a network stability test can be stated as:
The process of using programs and commands to make sure every router and other devices being used to connect an intranet to the Internet – be they behind or beyond the territorial firewall – is up and running. It also involves making sure all the authorized data on the network is safe – both in motion and in resting states.
What are the best ways to check network stability?
When examining a network’s stability, several things need to be done. They are as follows:
Checking network connectivity
The connection across a network should never be lost; it’s a must. Aside from that, it should be quick and not prone to packet drops. This may be accomplished using three techniques:
- There are programs available that aid network administrators in keeping track of their networks. The Paessler PRTG Network Monitor is one such tool. This is an all-in-one network monitoring suite of applications that continuously watches the connection between a host network and a test server, like Google, for example, which isn’t expected to go down – ever.
- You can do the test yourself using free tools like Ping and Tracert if you know even the basics of networking. If you don’t, keep reading; we’ll show you how to do it.
- Third-party websites such as Internet Health Test or Ping Can Be Useful may be used to check for internet connectivity and health. These are the most convenient methods, but they don’t provide comprehensive information about network connection problems – at least not for free.
Monitoring network data
The appropriate types of information should be transmitted over a network, not, for example, malicious data sent in by an attacker on the outside. Another case is that servers shouldn’t be backed up when they’re busy processing transactions during peak processing hours, since they might monopolize the bandwidth.
Administrators should track the data packets that flow through their networks. They can utilize a number of deep packet inspection and network analysis tools on the market to track traffic and filter it as needed.
Related: Best Networking Commands Every Windows Admin Should Use
Maintaining packet speeds across the connection
There should be no attrition or loss of data speeds. Packets shouldn’t be dropped because the network is too crowded, an access point isn’t functioning properly, or because the particular packets have been inadvertently blocked.
Network administrators should have a strategy in place for allocating bandwidth to different areas of their data transport – for example, allocate more bandwidth to VoIP and less to email traffic so that voice communication does not lag.
In addition, administrators may take certain defensive actions and corrective actions to address this concern.
Ensuring network protection
In addition, network administrators must ensure that there are no breaches in the system or unlawful usage of connected devices and data.
NIDS is a good tool for detecting intrusions.
Tools for Network Security and Stability
Finally, administrators realize that their networks will only last as long as the people who are not supposed to be on them are kept out. If intruders continue to disrupt data, settings, and permissions, they will be able to take control of the network.
They can then use it as a launching pad for additional assaults, break into connected devices, or simply crash it.
Tools like firewalls, anti-viruses, anti-malware, and IDS/IPS tools can all help you protect your network.
Let’s get into the technical side of PING and TRACERT, shall we?
What does PING do?
Pinging is a technique of sending packets to a target server and listening for a response. If all (100%) of the packets sent are acknowledged, the target is operational and there are no connectivity issues. On the other hand, any missed packet signals that there is an issue on the network somewhere along the route.
If the PING command indicates that 100% of the connections between the host computer and the target server are broken, it might indicate any (or all) of these links are down.
What does TRACERT do?
TRACERT is a packet-generating tool that sends packets to every router between the host computer and the target server.
However, in this situation, the packets are broadcast to every router along the way to the target machine and sent back to the host computer. Apart from confirming connectivity, each response also includes information on the next router in line so that subsequent packets can have an address to aim for in the queue.
It is also simple to figure out which routers are up, which one is taking too long to respond (the one with the longest reply time), and which one is down (the one that doesn’t send a response back).
How to use PING to test for network connectivity
PING is a handy utility that may be used from command-line interfaces (CLIs) on operating systems such as Windows, Linux, and macOS.
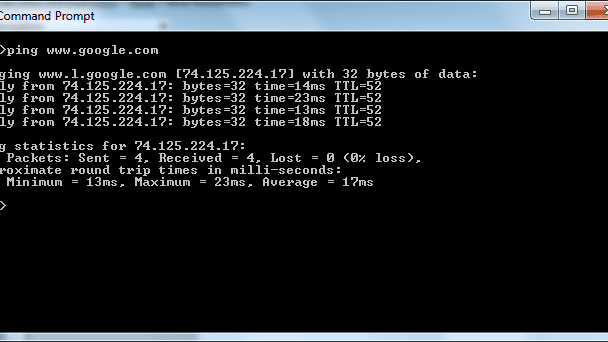
The steps involved in MS Windows are:
1. Open the command prompt.
2. Type “ping google.com” and hit Enter.
3. Check the results of the ping test.
Additional features may be included to the command by appending arguments to the fundamental structure, such as by using:
- ” -t.” When a remedy is implemented and you want to keep monitoring to see if the problem has been resolved, for example, you can use “-t” to ping a target continuously.
- ” -l.” The default packet size is 32, but it may be beneficial to use a different number.
- ” -n.” You can also use this argument to send a specific number of ping requests instead of the default four.
- ” -w.” This allows you to set a timeout period in milliseconds for each ping request.
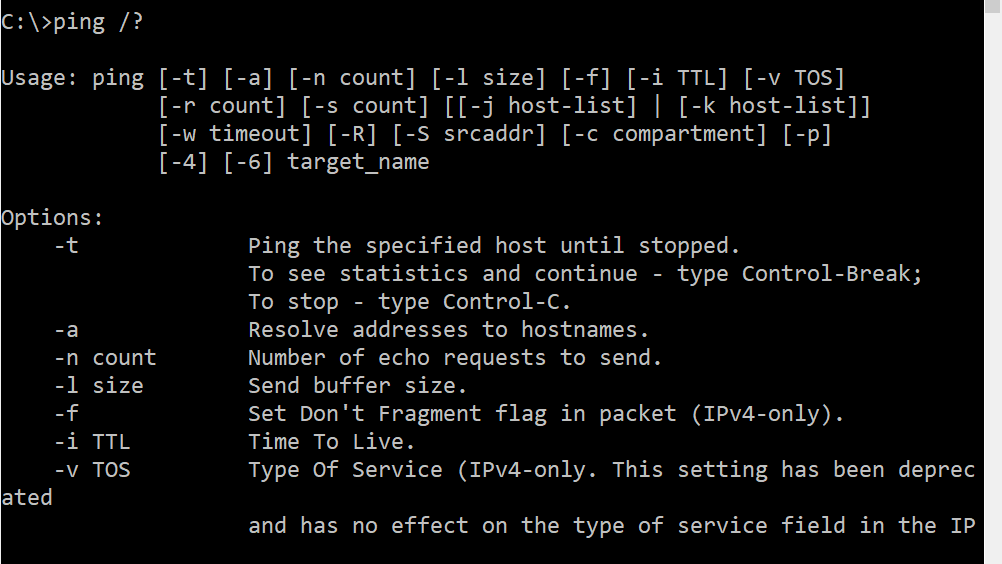
For a full list of all the arguments that can be used, simply type PING /? at the prompt.
How to use TRACERT to check for network or internet connectivity
TRACERT is a command-line tool that can be used to troubleshoot network connection issues. This program, in contrast to PING, does not just check the connection speed between two locations. It also examines each of the routers encountered along the trip as the data are carried from one to another via hops.
When a connection is lost, it can be detected by the lack of response from the device. This indicates that the silent device should be investigated.
Tracert is a Microsoft Windows command-line tool for determining the route that traffic takes to reach a destination. It’s pretty straightforward and easy to use, but it does have some limitations, especially in relation to latency or bandwidth requirements.
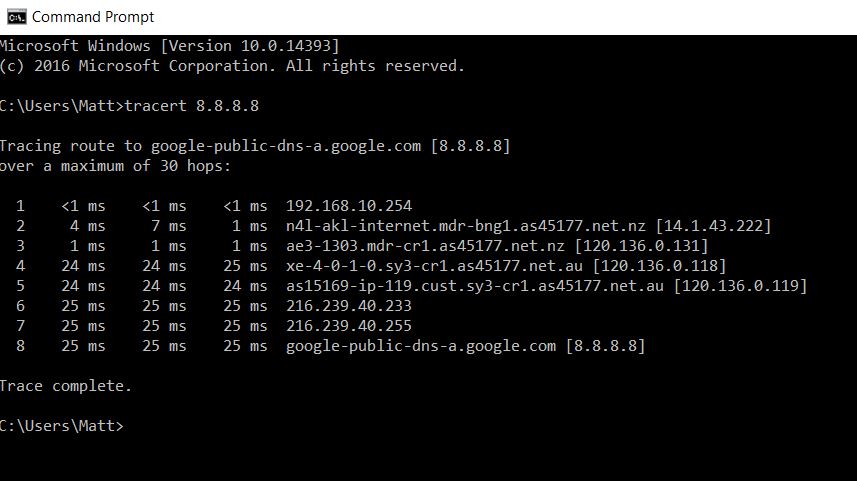
A TRACERT (traceroute) command should be run on any computer attempting to connect out of network using an IP address other than their own. The following are two examples of how to use the Tracert net utility:
- To find the route from your computer to the hostname “google.com”, open a Command Prompt and type: tracert google.com
- To find the route from your computer to the IP address “66.249.95.104”, open a Command Prompt and type: tracert 66.249.95.104
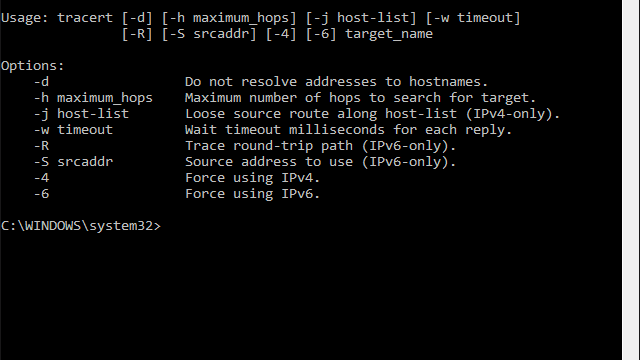
Many additional capabilities may be added to the command by appending arguments to the basic syntax, such as:
- “-h”, which specifies the maximum number of hops that can be used to reach the target device. Type TRACERT /? at the prompt for a complete list of all available arguments.
- -d, which bypasses the DNS resolution process and instead sends queries directly to an IP address.
- -j [host-list], which allows you to specify a loose source route as a list of up to nine IP addresses or hostnames in square brackets.
For a full list of all the arguments that can be used simply type TRACERT /? at the prompt.
Conducting network and internet stability tests
Now that we’ve seen all of the tools you’ll need to perform a network stability test, let’s look at how they fit into the overall plan. We’ve also seen that there is a group of tools available to accomplish each goal of a network stability test for those of us who don’t want to deal with command lines.
You may also use task schedulers or run them to check the status of your network’s stability at any moment.
Network Stability Test FAQs
How do you test network quality?
Latency, packet loss, and jitter are all used to evaluate network quality. The Ping application can reveal all of these indicators. The duration it takes to reach the destination is known as the round trip time. Lateness is a latency problem in one direction.
To get latency, divide the round trip time by two (or multiply by 2). Variance in delivery times is referred to as jitter.
The Ping results include minimal, maximum, and average RTT statistics. Larger numbers indicate higher jitter; for example, if the minimum and maximum are large and far apart from each other
How do I trace network latency?
To get an analysis of the latency on each leg between your computer and another node on the network, run pathping. This command may be issued from the command line, and it takes a parameter representing another node’s IP address, such as pathping 192.168.0.10.
Why is my jitter so high?
The most common reason for network jitter is heavy traffic. Traffic shaping, such as prioritized queuing on network devices, can improve performance for some applications while worsening jitter for others. Latency and jitter are critical not just for VoIP. As a result, many network administrators have placed a lot of importance on this traffic. VoIP traffic, however, occurs in bursts, so the transfer speeds of other programs will vary drastically since some of their packets will be delayed to make way for VoIP traffic bursts.
How to find out round-trip time?
The round trip time (RTT) is a measurement provided by both Ping and Pathping.




